[x]cube LABS and Grand Farm Announce the Launch of Report on Agritech 2021: Transforming Agriculture with Digital Technologies, at Cultivate Conference in July 2021
We are happy to share that [x]cube LABS has created an in-depth report for agribusinesses and related stakeholders, aimed at providing value-driven insights and recommendations. This report, to be released soon, is a one-of-its-kind collaboration with multiple experts in the industry. Upon release, It will serve as a valuable resource for stakeholders who are starting their agritech journey by providing them a comprehensive understanding of the agritech ecosystem and insights on strategies and technologies that deliver results.
Putting this report together has been a very exciting journey for us. During the process, we connected with stakeholders from various segments of the industry and gained deep understanding on the many problems faced by them. We leveraged our extensive experience of working with global enterprises in the agriculture space to solve these problems and consolidated the information into a single, detailed report. We believe this will help agribusinesses stakeholders such as enterprise owners, startups, government entities, researchers, investors, and the farming community to view the space as an integrated ecosystem, contrary to how it’s seen today- fragmented segments that work independently.
Check out our press release regarding this initiative below.
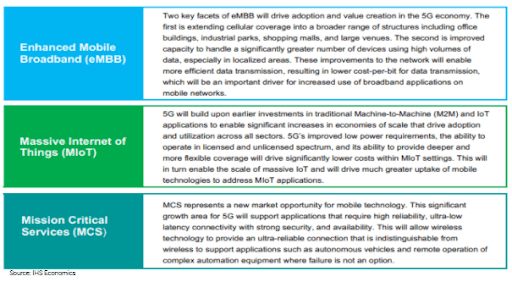
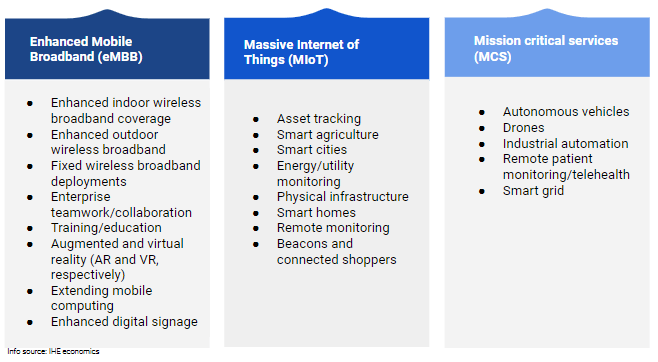
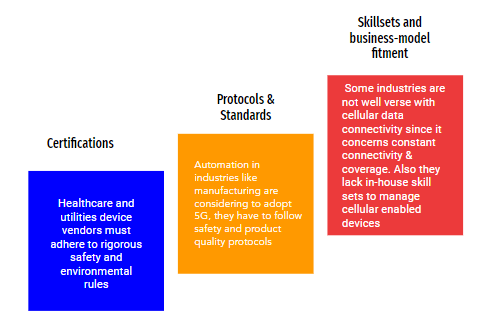
DALLAS, June 22, 2021 /PRNewswire/ — [x]cube LABS announced today the launch of an agriculture industry-focused report titled ‘Agritech 2021: Transforming Agriculture with Digital Technologies’ in collaboration with Grand Farm, on Thursday, July 15th, 2021 at the Cultivate Conference. Agriculture today faces challenges such as climate change, sustainability, shifting consumer demand falling grower income, and more. In this context, the report will provide a comprehensive overview of the industry and propose potential innovation opportunities that put the industry on the best course for the future. In addition, the report, which will be available for free, brings in detailed insights from a comprehensive survey conducted by [x]cube LABS, covering stakeholders across all key roles and segments of the industry. The report will feature insights from industry experts, showcase innovative Agritech use cases, and publish results from an independent study of global agriculture stakeholders.
Speaking to the press, Puneet Kalia, AgTech business leader at [x]cube LABS, said: “Multiple driving forces are transforming agriculture in significant ways, and this creates opportunities as well as significant challenges for stakeholders in this space. This report put together in collaboration with key players across the agriculture industry, will fill an important gap and offer a comprehensive view of the transformative landscape at large. We’re excited to launch this report at the Cultivate Conference.”
The Cultivate Conference, hosted by Grand Farm, is an event focused on emerging technologies in agriculture and features attendees from leading agri-tech firms and research institutes.
“We’re excited about this collaboration with [x]cube LABS,” said Andrew Jason, Grand Farm Ecosystem Builder. “As the industry is set to undergo drastic innovation, they are a great partner to be leading this report as they’ve been leading digital transformation for years.”
About Grand Farm
The Grand Farm Education and Research Initiative, energized by Emerging Prairie, capitalizes on the region’s potential and expertise in the agriculture and technology industries. The Grand Farm Initiative will accelerate the research and innovation into technology that will be present on the farm of the future – impacting North Dakota, the United States, and the World by solving challenges in the agriculture industry and developing new opportunities.
About [x]cube LABS
[x]cube LABS is a leading digital transformation company working across diverse industries, including agriculture. [x]cube LABS has helped agriculture stakeholders worldwide with digital solutions that resolve critical bottlenecks and develop innovative digital products to transform customer engagement and business operations. Located in the US, Europe, and Asia, [x]cube LABS has worked with more than 30 Fortune 2000 companies and has developed a reputation as a high-quality partner for building digital centers of excellence, customer experience transformation, and IoT implementations. For more information, visit: http://www.xcubelabs.com
 1-800-805-5783
1-800-805-5783